已经尝试,通过设备厂商自带程序检查硬件正常、更新网卡驱动(来源硬件厂商官网下载)、用过SFC命令验证系统完整性,均没有效果,有多台电脑出现这种情况,设备品牌有戴尔、联想、华为,系统为win11家庭版(硬件厂商出场自带),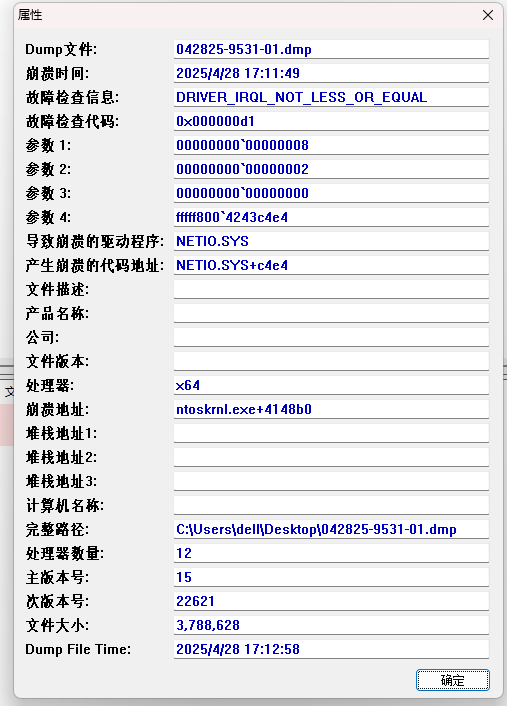
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
DRIVER_IRQL_NOT_LESS_OR_EQUAL (d1)
An attempt was made to access a pageable (or completely invalid) address at an
interrupt request level (IRQL) that is too high. This is usually
caused by drivers using improper addresses.
If kernel debugger is available get stack backtrace.
Arguments:
Arg1: 0000000000000008, memory referenced
Arg2: 0000000000000002, IRQL
Arg3: 0000000000000000, value 0 = read operation, 1 = write operation
Arg4: fffff8004243c4e4, address which referenced memory
Debugging Details:
------------------
KEY_VALUES_STRING: 1
Key : Analysis.CPU.mSec
Value: 1843
Key : Analysis.Elapsed.mSec
Value: 1863
Key : Analysis.IO.Other.Mb
Value: 1
Key : Analysis.IO.Read.Mb
Value: 1
Key : Analysis.IO.Write.Mb
Value: 11
Key : Analysis.Init.CPU.mSec
Value: 1234
Key : Analysis.Init.Elapsed.mSec
Value: 24175
Key : Analysis.Memory.CommitPeak.Mb
Value: 117
Key : Analysis.Version.DbgEng
Value: 10.0.27793.1000
Key : Analysis.Version.Description
Value: 10.2410.02.02 amd64fre
Key : Analysis.Version.Ext
Value: 1.2410.2.2
Key : Bugcheck.Code.LegacyAPI
Value: 0xd1
Key : Bugcheck.Code.TargetModel
Value: 0xd1
Key : Failure.Bucket
Value: AV_NETIO!StreamInvokeCalloutAndNormalizeAction
Key : Failure.Exception.IP.Address
Value: 0xfffff8004243c4e4
Key : Failure.Exception.IP.Module
Value: NETIO
Key : Failure.Exception.IP.Offset
Value: 0xc4e4
Key : Failure.Hash
Value: {c2ca2d1f-cfdc-88d5-c7bc-7693b8f0de04}
Key : WER.OS.Branch
Value: ni_release
Key : WER.OS.Version
Value: 10.0.22621.1
BUGCHECK_CODE: d1
BUGCHECK_P1: 8
BUGCHECK_P2: 2
BUGCHECK_P3: 0
BUGCHECK_P4: fffff8004243c4e4
FILE_IN_CAB: 042825-9531-01.dmp
FAULTING_THREAD: ffff888edddf1040
READ_ADDRESS: fffff8003d91c470: Unable to get MiVisibleState
Unable to get NonPagedPoolStart
Unable to get NonPagedPoolEnd
Unable to get PagedPoolStart
Unable to get PagedPoolEnd
unable to get nt!MmSpecialPagesInUse
0000000000000008
BLACKBOXBSD: 1 (!blackboxbsd)
BLACKBOXNTFS: 1 (!blackboxntfs)
BLACKBOXWINLOGON: 1
CUSTOMER_CRASH_COUNT: 1
PROCESS_NAME: System
TRAP_FRAME: ffff878c3fee52f0 -- (.trap 0xffff878c3fee52f0)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=0000000000000000 rbx=0000000000000000 rcx=ffff878c3fee55f8
rdx=ffff888eee8e4b20 rsi=0000000000000000 rdi=0000000000000000
rip=fffff8004243c4e4 rsp=ffff878c3fee5480 rbp=ffff878c3fee54f9
r8=ffff888eee8e4b20 r9=00000000000005a0 r10=ffff888ef955a670
r11=0000000000000000 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei pl zr na po nc
NETIO!StreamInvokeCalloutAndNormalizeAction+0x5c:
fffff800`4243c4e4 488b4808 mov rcx,qword ptr [rax+8] ds:00000000`00000008=????????????????
Resetting default scope
STACK_TEXT:
ffff878c`3fee51a8 fffff800`3d02a829 : 00000000`0000000a 00000000`00000008 00000000`00000002 00000000`00000000 : nt!KeBugCheckEx
ffff878c`3fee51b0 fffff800`3d025c89 : 00000000`000004c0 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiBugCheckDispatch+0x69
ffff878c`3fee52f0 fffff800`4243c4e4 : ffff878c`3fee55c0 ffff888e`ee8e4b20 ffff878c`3fee55c0 ffff888e`ee8e4b20 : nt!KiPageFault+0x489
ffff878c`3fee5480 fffff800`4243bd8b : ffff888e`ee8e4b20 ffff888e`ee8e4b20 ffff888e`f955a601 00000000`00000000 : NETIO!StreamInvokeCalloutAndNormalizeAction+0x5c
ffff878c`3fee5550 fffff800`4243992b : ffff888e`dc5e0014 fffff800`3e6e2300 ffff888e`00000004 ffff878c`3fee5ee8 : NETIO!StreamProcessCallout+0x2c7
ffff878c`3fee5680 fffff800`424389dd : 00000000`00000014 ffff878c`3fee5ee8 ffff878c`3fee5f10 ffff878c`3fee5d90 : NETIO!ProcessCallout+0xa4b
ffff878c`3fee5800 fffff800`424376ee : 00000000`00000005 ffff878c`3fee5f10 ffff888e`ddbe4aa0 ffff888e`da402000 : NETIO!ArbitrateAndEnforce+0x59d
ffff878c`3fee5930 fffff800`424351d5 : 00000000`00000050 00000000`00000001 ffff888e`e1b0d400 00000000`00000001 : NETIO!KfdClassify+0x33e
ffff878c`3fee5ce0 fffff800`42434dd8 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : NETIO!StreamClassify+0x279
ffff878c`3fee5e80 fffff800`42434a47 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`000004c0 : NETIO!StreamCommonInspect+0x2ac
ffff878c`3fee6270 fffff800`4254b738 : ffff878c`3fee6300 ffff888e`e61d9a00 00000000`00000000 ffff888e`ea618950 : NETIO!WfpStreamInspectReceive+0x157
ffff878c`3fee62f0 fffff800`4254b5ab : ffff888e`e61d9ab0 00000000`00000000 ffff878c`3fee6438 ffff888e`e61d9ab0 : tcpip!InetInspectReceive+0x80
ffff878c`3fee63a0 fffff800`425f1a2b : ffff878c`3fee6500 ffff888e`dc9e9c50 ffff888e`ea8ce530 ffff888e`ea8ce530 : tcpip!TcpInspectReceive+0xaf
ffff878c`3fee6420 fffff800`425299f4 : ffff878c`3fee66a0 ffff888e`e61d9ab0 00000000`00000000 00000000`00000000 : tcpip!TcpProcessFastDatagramBatch+0x87
ffff878c`3fee6470 fffff800`42527129 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : tcpip!TcpTcbReceive+0x454
ffff878c`3fee6630 fffff800`4252611f : ffffbb00`d0912322 00000000`00000018 ffffbb00`d0910a62 ffff888e`ddfc3148 : tcpip!TcpMatchReceive+0x519
ffff878c`3fee6800 fffff800`42524fa6 : ffff888e`ddafd160 fffff800`4256bb01 00000000`00000001 ffff888e`e19772c9 : tcpip!TcpReceive+0x35f
ffff878c`3fee6910 fffff800`42562c86 : 00000000`00000000 00000000`00000000 00000000`00000014 ffff888e`ddfc3148 : tcpip!TcpNlClientReceiveDatagrams+0x16
ffff878c`3fee6940 fffff800`42562a79 : 00000000`00000000 ffff888e`00000006 ffff888e`ddfc3000 ffff878c`3fee6a90 : tcpip!IppProcessDeliverList+0xb6
ffff878c`3fee6a30 fffff800`4256174b : fffff800`427339d0 ffff888e`dd1e98a0 ffff888e`ddfc3000 ffff878c`3fee6b70 : tcpip!IppReceiveHeaderBatch+0x3a9
ffff878c`3fee6b20 fffff800`425cd80a : ffff888e`e3059220 ffff888e`e1a51da0 00000000`00000001 ffff888e`00000000 : tcpip!IppReceivePackets+0x50b
ffff878c`3fee6c50 fffff800`4257a0bb : ffff888e`e3059220 ffff888e`e1a51da0 00000000`00000000 00000000`00000000 : tcpip!IpFlcReceivePreValidatedPackets+0x11ca
ffff878c`3fee6de0 fffff800`3ce39cda : 00000000`00000000 fffff800`42579f70 ffff888e`dddf10b4 00000000`00000002 : tcpip!FlReceiveNetBufferListChainCalloutRoutine+0x14b
ffff878c`3fee6f30 fffff800`3ce39c4d : fffff800`42579f70 ffff878c`3fee7078 ffff888e`ddbc31a0 00000000`00000000 : nt!KeExpandKernelStackAndCalloutInternal+0x7a
ffff878c`3fee6fa0 fffff800`42598b80 : ffff888e`dccec800 fffff800`4243549e fffff800`3d90e080 00000000`00000000 : nt!KeExpandKernelStackAndCalloutEx+0x1d
ffff878c`3fee6fe0 fffff800`422b2701 : 00000000`00000000 fffff800`57781ca7 00000000`00000000 00000000`00000000 : tcpip!FlReceiveNetBufferListChain+0x530
ffff878c`3fee72c0 fffff800`422b211a : ffff888e`dececb30 ffff888e`e1aa0801 ffff888e`00000000 fffff800`00000002 : ndis!ndisMIndicateNetBufferListsToOpen+0x141
ffff878c`3fee73a0 fffff800`422d6bb1 : ffff888e`e185c1a0 fffff800`00000000 ffff888e`00000000 ffff888e`e185c1a0 : ndis!ndisMTopReceiveNetBufferLists+0x24a
ffff878c`3fee7480 fffff800`422d661f : 00000000`00000000 ffff878c`3fee7570 fffff800`422b1ed0 fffff800`42440c90 : ndis!ndisCallReceiveHandler+0xb9
ffff878c`3fee74d0 fffff800`422d69d7 : ffff888e`e159a9d0 00000000`00000000 00000000`00000000 fffff800`3a321180 : ndis!ndisCallNextDatapathHandler<2,void * __ptr64 & __ptr64,void (__cdecl*& __ptr64)(void * __ptr64,_NET_BUFFER_LIST * __ptr64,unsigned long,unsigned long,unsigned long),void * __ptr64 & __ptr64,_NET_BUFFER_LIST * __ptr64 & __ptr64,unsigned long & __ptr64,unsigned long & __ptr64,unsigned long & __ptr64>+0x3f
ffff878c`3fee7520 fffff800`422d670e : ffff888e`e185c1a0 fffff800`422b1ed0 ffff888e`e185c1a0 00000000`00000001 : ndis!ndisIterativeDPInvokeHandlerOnTracker<2,void __cdecl(void * __ptr64,_NET_BUFFER_LIST * __ptr64,unsigned long,unsigned long,unsigned long)>+0x8b
ffff878c`3fee7590 fffff800`422d6c76 : ffff888e`e1955290 00000000`00000000 00000000`00000001 ffff888e`e1a51da0 : ndis!ndisInvokeIterativeDatapath<2,void __cdecl(void * __ptr64,_NET_BUFFER_LIST * __ptr64,unsigned long,unsigned long,unsigned long)>+0xe2
ffff878c`3fee7600 fffff800`422b3866 : 00000000`00029bf5 00000000`00000001 00000000`00000000 fffff800`3ce38648 : ndis!ndisInvokeNextReceiveHandler+0xa6
ffff878c`3fee7660 fffff800`8a557c9c : ffff888e`e1956002 ffff888e`e1956000 00000000`00000000 ffffbb00`d0910a00 : ndis!NdisMIndicateReceiveNetBufferLists+0x116
ffff878c`3fee76f0 ffff888e`e1956002 : ffff888e`e1956000 00000000`00000000 ffffbb00`d0910a00 00000000`00000001 : rt640x64+0x27c9c
ffff878c`3fee76f8 ffff888e`e1956000 : 00000000`00000000 ffffbb00`d0910a00 00000000`00000001 00000000`00000000 : 0xffff888e`e1956002
ffff878c`3fee7700 00000000`00000000 : ffffbb00`d0910a00 00000000`00000001 00000000`00000000 00000000`00000001 : 0xffff888e`e1956000
SYMBOL_NAME: NETIO!StreamInvokeCalloutAndNormalizeAction+5c
MODULE_NAME: NETIO
IMAGE_NAME: NETIO.SYS
IMAGE_VERSION: 10.0.22621.1431
STACK_COMMAND: .process /r /p 0xffff888eda4ea040; .thread 0xffff888edddf1040 ; kb
BUCKET_ID_FUNC_OFFSET: 5c
FAILURE_BUCKET_ID: AV_NETIO!StreamInvokeCalloutAndNormalizeAction
OS_VERSION: 10.0.22621.1
BUILDLAB_STR: ni_release
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
FAILURE_ID_HASH: {c2ca2d1f-cfdc-88d5-c7bc-7693b8f0de04}
Followup: MachineOwner
